Ukrainian intelligence hacks Russia's strategic aircraft manufacturer

Ukraine’s intelligence services have hacked into the systems of Russia’s United Aircraft Company Tupolev (Design Bureau) – one of the country's key companies involved in strategic aircraft.
Source: a source of Ukrainska Pravda in Ukraine's Defence Intelligence (DIU)
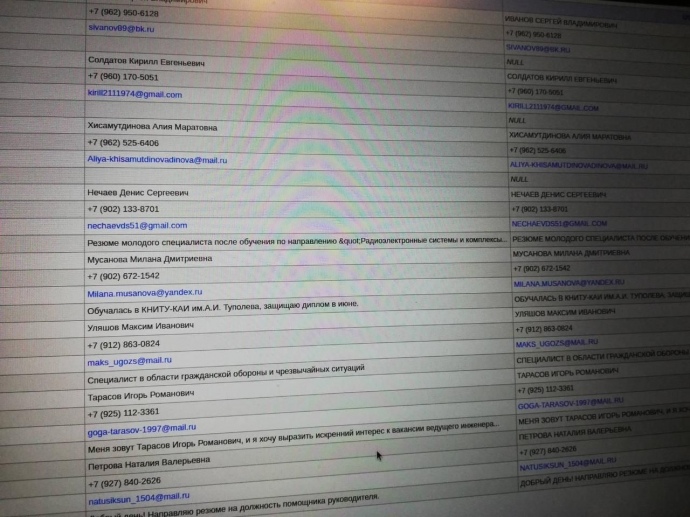
Details: The intelligence source revealed that the operation resulted in access to a trove of data, including internal communications, personal information about employees, home addresses, engineers' CVs, procurement documents and minutes from closed meetings.
The source said Ukrainian intelligence had been monitoring the company's document flow for some time. The acquired data makes it possible to identify individuals directly involved in servicing Russia's strategic aircraft.
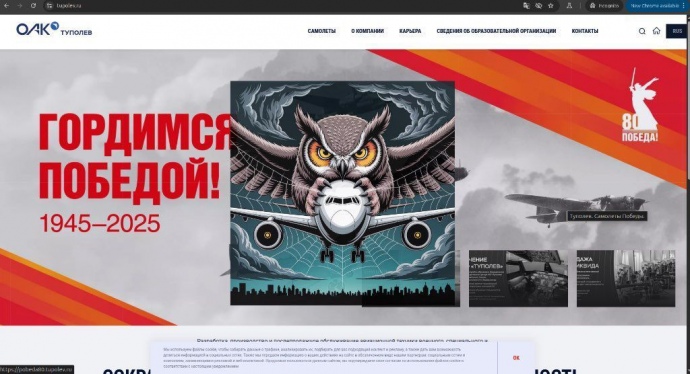
To mark the completion of the operation, Ukrainian cyber specialists posted an image on Tupolev's official website showing an owl clutching a Russian aircraft – a symbol of the attack.
Quote from the source: "There’s virtually no secret left in Tupolev's operations as far as Ukrainian intelligence is concerned. In particular, we now possess comprehensive information about the individuals directly involved in maintaining Russia's strategic aircraft. The results will be evident both on the ground and in the sky."
Background: Russia's Tupolev Design Bureau has been under international sanctions since 2022 for its involvement in Russia's war of aggression against Ukraine.
Support Ukrainska Pravda on Patreon!